This blog post looks at the Hybrid SOC model, what it is and why it is worth considering for your operation.
There are several outsourcing models to choose from when contracting for security operations, ranging from keeping it all in-house to outsourcing everything to a managed security services provider (MSSP). In a previous post we looked at the difference between outsourcing and insourcing. Let’s now look at the Hybrid SOC in more detail to understand why so many organisations are choosing this option.
What is a Hybrid SOC?
The Hybrid SOC model isn’t new. It is how many companies have been outsourcing IT services for years, as it offers flexibility, scalability and cost effectiveness. However, it does require careful planning and effort from your organisation to ensure it achieves the goals set in the contract.
The Hybrid SOC model has a simple premise: some aspects of the operation remain in-house, while others are delivered by the MSSP. In Figure 1 below is an example of the building blocks covered in one such services contract.
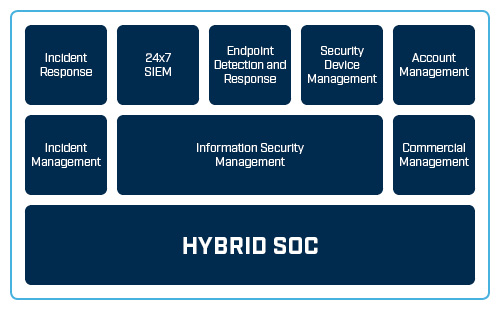
Figure 1 Example architecture for a Hybrid SOC
In Figure 1, the information security management capability is retained in-house. This allows the organisation to control the outcomes defined in the information security management system (ISMS) and places responsibility for those outcomes with the in-house information security manager. The information security manager looks after the extended security team including the MSSP services integrated into the security programme.
In the example shown the information security manager takes on the role of cultural ambassador for the organisation’s security programme, ensuring the organisation’s values and principles are adhered to by all contractors, MSSPs, service providers, vendors and partners.
To get the most from each of the security programme’s stakeholders, the information security manager should encourage a “one team” approach, to break down any perceived division between permanent employees and contractors. If this is not managed effectively, permanent staff often feel the MSSP is taking their jobs and they become obstructive and uncooperative, while trying to undermine the MSSP at every juncture.
The information security manager needs to report to the board on matters of compliance and risk, which goes without saying, but also finding a way to humanise the security capability and report on organisational culture and teamwork issues, along with partnering successes, which will resonate with executive leadership teams.
What Security functions must remain In-House?
In Figure 1, two additional capabilities are also retained by the organisation: commercial management (the only function that must remain in-house) and incident management. In this case, the incident management function is retained by the organisation, but is supported by the MSSP’s expert incident response service. This makes sense for some organisations because managing a major incident requires close liaison with different internal stakeholders, such as marketing and communications, the board, legal and financial team and units affected by the breach, as well as third-parties, such as law enforcement and the privacy regulator.
In Figure 1, the outsourcer has responsibilities to deliver a fully staffed 24x7x365 SOC, along with a managed SIEM and supporting technology such as endpoint detection and response along with security device management. The MSSP must deliver these services against the service levels specified in their contract, so they need to manage their shift rosters to ensure full 24x7x365 coverage, considering sick leave, holidays and staff movements. The information security manager will set those SLAs in the contract negotiations, along with key performance indicators (KPIs) that can measure the efficacy of the MSSP’s service delivery.
Several supporting services, as shown in Figure 1, have also been outsourced to this MSSP: endpoint detection and response and security device management. The MSSP’s responsibility is to provide the best threat detection capabilities on the market to the organisation’s endpoints (laptops, desktops, mobile devices and servers), plus demonstrable KPI reporting to show they meet the terms of the engagement.
Security device management is also included in this outsourcing contract, where the MSSP runs the organisation’s firewalls, intrusion prevention systems, web and mail gateways, network proxies, wireless access points, web application firewalls and anything else that provides a security function.
Importantly, the information security manager has retained control over the outcomes and considers the MSSP as an extension of its own security team. The hybrid approach works best as a partnership rather than a “them and us” model, since a close working relationship and a true partnership will yield the best results.
Who takes responsibility for technology in a Hybrid SOC?
Before approaching the market, it’s crucial to decide whether or not to take responsibility for the provision and selection of technology.
By asking your MSSP to use your existing or chosen technology, they may be forced to adapt their tried and tested service model to a different vendor’s equipment; this can lead to inefficiencies and mismatches in service coverage between their clients. Furthermore, this model also places the burden of vendor management on you the contracting organisation, which can be troublesome in times of technical issues.
By leaving the product selection to the MSSP, they will usually have a preferred solution that is used across all their clients, which offers great efficiency and also gives responsibility for vendor management to the MSSP.
How to deal with overlapping technology contracts
In some cases, organisations might already have a SOC, with a SIEM capability established, but due to manpower and service coverage they have decided to outsource. In this case, the technology has already been procured under a multiyear arrangement, so the MSSP could come in and run the on-premise technology until the contract runs out. At that stage, the contract could change to move to the MSSP’s preferred technology model. This is a normal occurrence in ICT outsourcing, since the management of ICT services often waxes and wanes from insourcing to outsourcing and across different service providers, so technology contracts often overlap.
If the information security manager prefers a specific security technology, such as a favoured SIEM or firewall vendor, then it pays to approach the vendor and ask which MSSPs they work with. Quite often, vendors will have a few companies they prefer to recommend, who they believe have the best experience in running their tools, or whom they know provide excellent services, so this kind of recommendation is worth getting.
If the organisation must run a competitive tendering process for provision of ICT services, a private, invitation-only request for tender can be used, where only MSSPs offering the preferred technology and services will be invited to respond. This allows the organisation to get the best price, but provides some level of guarantee on the desired outcomes, based on the specific technology products.
Measuring the Performance of your MSSP
The most important consideration when managing an MSSP contract is getting the SLAs and the KPIs right. These must be set against your organisation’s security goals, and be easily measured and reported on. At the end of the day, value for money and appropriate outcomes should drive outsourcing behaviours.
Hybrid SOC – The Best of Both Worlds
It’s easy to see why Hybrid SOC is a popular model for contracting MSSPs. It is flexible enough to give you, the contracting organisation control, while leaving the MSSP to worry about shift rosters, staff training and technology management. Moreover, most MSSPs also offer a portfolio of additional services, including manpower-intensive services such as penetration testing, which can be easily built into your contract.
 About Huntsman
About Huntsman



