In a previous blog post we looked at how a security scorecard can be used to monitor your organisation’s compliance against a predefined set of controls, such as the Australian Cyber Security Centre’s (ACSC) recommended Essential Eight (E8). By selecting a security framework like E8 you’ve already made a risk management decision; you’ve acknowledged a set of risks against which you want to protect your enterprise. But don’t stop there. By routinely making these measures you can benchmark your security posture over time for continuous risk management and quality improvement purposes.
The ACSC has assessed that by implementing the E8 controls across your enterprise, it will reduce the risk of a successful cyber-attack by 85%. Using a security scorecard to provide real-time risk reporting against these controls ensures that your security team is able to identify and focus their risk management efforts on those residual risks threatening the enterprise. Using the continuous scorecard information, these audit and risk management “dance partners” enhance your security team’s risk management operations and deliver executive insights into the cyber resilience of the enterprise. This blog explores the process with a worked example.
Step 1 – Monitoring Controls Compliance
To recap, ACSC’s Essential Eight comprises eight critical risk mitigation controls that include for example, the timely patching of applications and operating systems, robust backups and application hardening. By implementing these controls your security team is confirming the key set of risks it is seeking to defend against.
The monitoring of the E8 controls allows the ongoing measurement of the success of managing those risks. It also provides early identification of any operational risks that may have circumvented the controls; which require specific risk-based management by the Security Operations team.
An example of how the process works
We’ll use operating systems patching as the basis for a worked example as we walk through this process. Operating systems patching is an important security control, since operating systems vulnerabilities are often the weakness in cyber defences that lets an attacker in. Timely patching, especially for critical vulnerabilities, means your organisation must:
- Know that vulnerabilities have been discovered;
- Know the vendor has released a patch to fix the problem;
- Know which systems need to be patched;
- Have the tools and processes to quickly roll out the patch;
- Have the tools and processes to monitor patch status.
Let’s consider a hypothetical vulnerability in Windows 10; it affects every single desktop and laptop in your business and could allow remote attackers to seize control of the computer and access anything within your enterprise. The vendor has labelled this software bug as a critical vulnerability, issuing an advisory that recommends every Windows 10 installation should be updated as soon as practicable.
Let’s assume your security team monitors vendor security bulletins and, has already downloaded the patch. How do they know which systems need to be patched? In most cases, your enterprise administrators will use tools such as Microsoft’s System Centre Configuration Manager (SCCM) to deploy patches to Windows-based computer systems, and the configuration management capability can ensure patch deployments have been rolled out across the fleet.
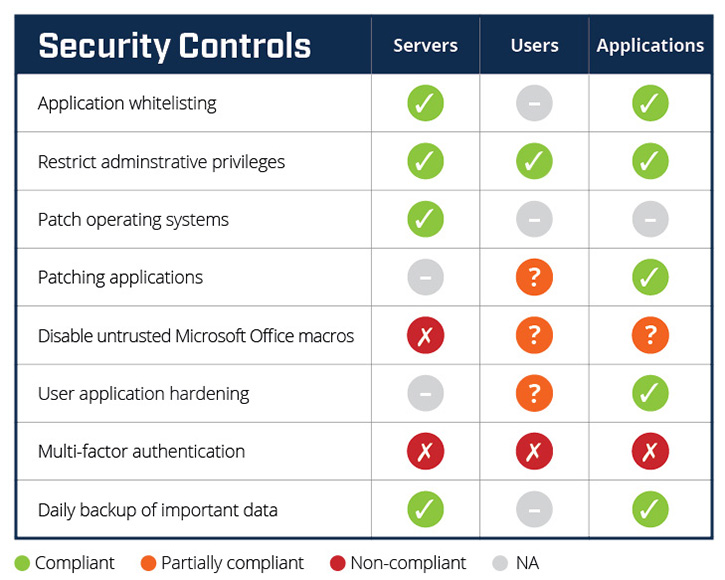
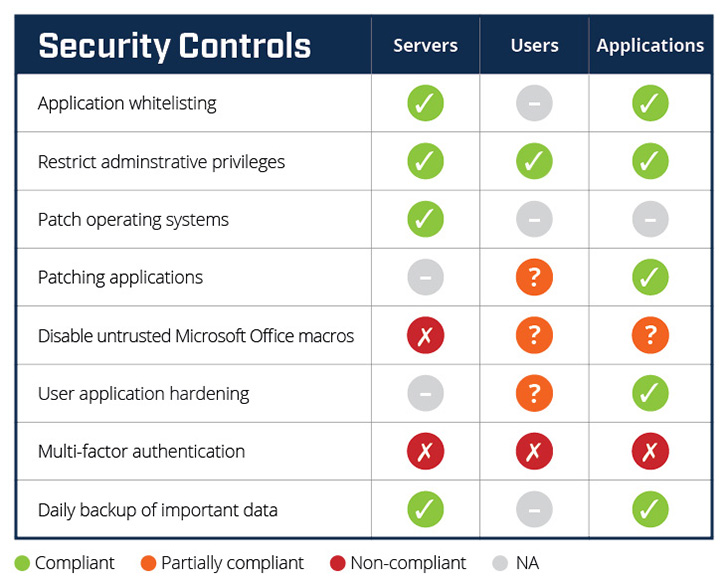
The Huntsman Security Scorecard automatically collects the patch management status from your enterprise, aggregates that information and calculates a patch score which is visualised using a simple RAG (red/amber/green) traffic-light metaphor, as shown in Figure 1. In this example, we can quickly see Patch operating systems – Servers is compliant while the same level of reporting for desktops/laptops is unsatisfactorily, unavailable. The security team can now prioritise work on patching desktop/laptop security targets.
Step 2 – Risk Management
Before this vulnerability was discovered, the scorecard for Patch operating systems registered green (compliant), that is to say, the risks associated with an inappropriate level of patching were, in effect, managed. Once the vulnerability was discovered, however, the traffic-light turned red, indicating an increased level of cyber security risk.
Each scorecard metric is a hard number representing the proportion of compliant to non-compliant data points for that control. It is suitable for comparative measurement and ranking; the graduated traffic-light visualisation on the other hand can be matched to suit the particular risk appetite of your organisation.
There are a number of risk vectors that should be considered in any risk-based assessment, interpretation or visualisation of the scorecard metrics. Commonly referred to as ‘The Five Knows’:
- The value of the assets you are protecting;
- Who has access to those assets;
- Where your assets are;
- Who is protecting your data; and
- How well is it protected
Automated Reporting of Key Cyber Metrics
Continuous compliance reporting against the controls automatically populates the scorecard. This enables your security team to easily prioritise and focus their risk management efforts on identified risks. For senior executives (CISOs and board members), the benefit is a clear understanding of your organisation’s current and emerging risk exposures based on live security metrics.
To further assist risk management efforts, the security scorecard enables your security team to decide the nature of a temporary workaround, if needed, and manage the alerted risk until the patch can be fully deployed. For example, if the vulnerability is discovered yet no patch is available, risk-based options can be assessed to help the security team, in conjunction with other stakeholders, decide the preferred course for a particular threat. It could be a few weeks until the patch becomes available, so the scorecard enables the regular assessment of each of the following options:
- Monitor the risk: Make no systems changes since the patch will be released soon. Status remains RED.
- Reduce functionality: Critical assets are at risk, and RED is unacceptable. It may be preferable to block Internet traffic to that system, thus making it unavailable to remote users for a time;
- Increase monitoring and alerting: Critical assets are at risk and while this is a concern, however, remote users are critical to the business’s operations. As a result, heightened risk management efforts including continuous security monitoring and alerting will allow the security team to protect the impacted system until a patch becomes available.
Workarounds are an important tool of the risk management approach, yet their efficacy is best determined when risk management options are continuously informed through the scorecard and other relevant information.
Practice Makes Perfect – The Ongoing Steps of Continuous Improvement
The greatest value the security scorecard offers is that it keeps you informed of your current security posture and the residual level of operational risk in your security operations over time. It measures the on-going success of:
- Your control efforts against risks; and
- Your broader security management strategy.
It does this by highlighting the relevant risk information necessary to initiate risk management activities against an outstanding risk and it is the starting point and catalyst in risk management efforts across all security environments.
The security scorecard will empower your security team with relevant context-aware information and give stakeholders measurable information upon which improved security decisions can be made. At the same time, your operations managers can implement informed risk management strategies to mitigate risks and senior managers can make informed decisions to best suit your business’s needs…… one, two cha cha cha!!!
 About Huntsman
About Huntsman