Critical infrastructure (CI) systems are prime targets for cyber-attack from overseas adversaries as the mass disruption from a successful attack could seriously cripple a country’s economy and national security. How prepared is your critical infrastructure to defend against international hackers and what can you do to build effective security controls?
Critical Infrastructure – A Prime Cyber Attack Target
From a legal perspective, in June 2018, the Australian government introduced new laws to make sure saboteurs who hack our nation’s critical infrastructure can be jailed for up to 15 years. This legislative change was welcomed as the government acknowledged the changing nature of warfare to include battles fought in cyberspace. Even traditional kinetic warfare starts with the first volley often fired electronically at the target’s critical infrastructure.
The Trusted Information Sharing Network [1] (TISN) for Critical Infrastructure defines CI as:
“Those physical facilities, supply chains, information technologies and communication networks, which if destroyed, degraded or rendered unavailable for an extended period, would significantly impact on the social or economic well-being of the nation, or affect Australia’s ability to conduct national defence and ensure national security.”
CI is a prime target for a variety of threat actors who would benefit from disrupting or destroying nationally important assets. By targeting CI providers’ Internet access, information and communications systems and industrial control systems (ICS), attackers could cripple a country’s ability to act, so cyber security is vitally important for these providers to get right.
Challenges with ICS and SCADA

ICS and Supervisory Control & Data Acquisition (SCADA) systems are both commonplace in CI providers, since these control systems manage the interfaces between technology and the physical world. Many of these systems are in out in the field, extending the CI providers’ services into remote locations, so it is vital that they are reliable and robust under normal operating conditions.
They are typically built to last against the elements and often operate in hostile conditions. Hence many of these systems have been in place for decades. But as we know with ICT systems, the older they are, the more likely there will be vulnerability in their code base. Yet many of these systems are not managed by the IT team, since they are off the corporate network and cannot be remotely patched, so they remain in place, performing their critical task, exposed to some of the most devastating attacks known.
If these ICS and SCADA systems can’t be patched and remain high-risk for CI providers, how can they build security systems to protect them?
Monitoring ICS and SCADA Systems for Compliance
When you deploy an ICS or SCADA system, there are several administrative and management considerations you must embed in that design that relate to security:
- How do you manage security in normal day-to-day operations?
- How do you manage security exceptions (failures or attacks)?
These days, most CI providers have reasonable security solutions on the IT side of the business. Many will have a Security Operations team that monitor servers and network devices for signs of attack and incident response procedures in place to eradicate the hacker from the systems when detected. Yet, most of these same organisations don’t extend their security monitoring to the Operational Technology (OT) arm of the business since, it has always been considered too hard to manage in the same way as IT.
Take Control of the Security Controls
Taking a control centric view of the world can help, especially if you speak a common language, such as the Australian Signals Directorate’s Essential Eight (more on that below). Backup is a useful control, whether it’s in IT or OT, and monitoring the efficacy of your backup solution should be inherent in your cyber strategy.
If your security operations team already monitors the IT backup systems, then focus on working with your OT engineers to see how events from their ICS/SCADA systems can be routed back to your monitoring system.
These days, modern Security Information and Event Monitoring (SIEM) technology comes with dozens of interfaces for system logs, so there are few endpoints that they won’t directly interface with. By channelling the events from ICS/SCADA systems back to the SIEM, any controls compliance monitoring you do can also apply to your OT network systems. This helps keep both sides of the business aligned with your security objectives and ensures the critical end of the business remains safe from cyber-attack.
The Essential Eight[2] Security Controls
Australian Signals Directorate’s (ASD) Essential Eight Strategies to Mitigate Cyber Security Incidents is a published list of prioritised mitigation strategies that any organisation can use to protect their systems against cyber threats. ASD’s experience of using the controls, estimates that adoption can fend of 85% of targeted attacks – that is worth investing in.
Many Australian organisations have opted to use the Essential Eight as the basis for their cyber protection mechanisms, which is a great start to bolstering your national cyber readiness. However, there is more to securing systems than simply building in security controls; you need to monitor their ongoing efficacy and coverage.
For example, your backup systems may have undergone initial testing to ensure they were running effectively when they were installed. However, ICT systems, as we all know, breakdown over time, as does computer hardware. Even a simple backup solution could have a series of vulnerabilities appear over the course of a few months that now sees it wide open to attack.
How do you monitor the state of your ICS and SCADA systems when the world is continually shifting under your feet? This is where protective monitoring and proactive alerting comes in.
Huntsman Security and Essential Eight Monitoring
Huntsman Security’s Essential Eight Compliance solution provides real-time alerting on each of the Essential Eight controls, with accurate reporting that your security operations team can use to ensure compliance and make rapid decisions that enhance your cyber resilience. The technology collects and analyses events from your ICS/SCADA infrastructure, systems, services and applications to deliver benchmarking against the ASD’s Essential Eight risk mitigation strategies.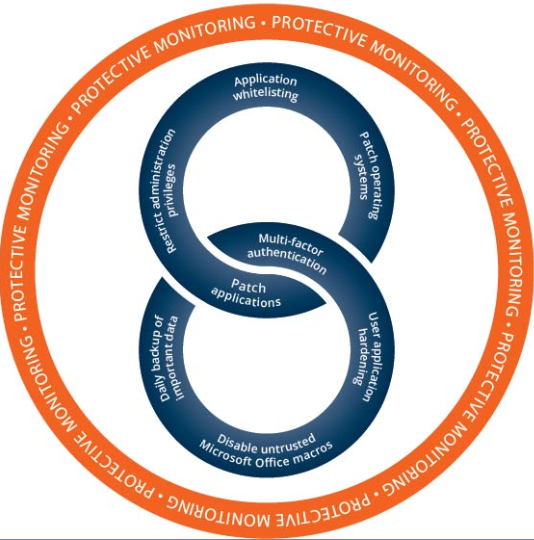
[1] https://www.tisn.gov.au/Pages/Critical_infrastructure.aspx
[2] https://www.acsc.gov.au/publications/protect/essential-eight-explained.htm
 About Huntsman
About Huntsman




