The Financial Reporting Council (FRC) is responsible for corporate governance, reporting and audit in the UK and has been consulting on the role of technology in audit processes.
On the one hand there is a recognition that technology can assist audits, providing the ability to automate data gathering or assessment to increase quality, remove subjectivity and make the process more trustworthy and consistent.
Both the Brydon review and the latest AQR thematic posit a link between enhanced audit quality and the increasing use of technology. This goes beyond efficiency gains from process automation and relates, in part, to the larger volume of data and evidence which can be extracted from an audited entity and the sophistication of the tools available to interrogate it.
As one example, the PCAOB in the US has for a while advocated for the provision of audit evidence and reports to be timely (which implies computerisation and automation) to assure that risks are being managed, and for the extent of human interaction with evidence or source data to be reflected to ensure influence is minimised (the more that can be achieved programmatically and objectively the better).
However, technology may obscure the nature of analysis and decision making and hence create a barrier to fully transparent audits compared to more manual (yet labour intensive) processes. There is also a competition aspect between larger firms and smaller ones as regards access to technology:
Brydon raised concerns about the ability of challenger firms to keep pace with the Big Four firms in the deployment of innovative new technology.
The discussion document and call for views (which has now passed) can be found here.
FRC discussion paper – some of the issues
The consultation paper covers issues, and asks questions, in a number of areas. Examples include:
- The use of AI and machine learning that collect or analyse evidence and due to the continual learning nature, their criteria for assessment may be difficult to establish or could change over time.
- The data issues around greater access to networks and systems putting information at risk (e.g. under GDPR) or a reluctance for audited companies to allow audit firms to connect or install software/technologies into their live environments.
- The nature of technology may mean it is harder for auditors to understand or establish the nature of data collection, analysis or decision making.
- The ongoing need to train auditors on technologies that might be introduced, so they can utilise them in a way that generates trusted outputs.
Clearly these are real issues – for a process that aims to provide trustworthy, objective, transparent and repeatable outputs – any use of technology to speed up or improve the process must maintain these standards.
Audit technology solutions in cyber security
The cyber security realm has grown to quickly become a major area of risk and hence a focus for boards, technologists and auditors alike.
The highly technical nature of threats and the adversarial nature of cybers attackers (who will actively try and find/exploit control failures) means that technology solutions that identify weaknesses and report on specific or overall vulnerabilities are becoming more entrenched in the assurance process within this discipline.
While the audit consultations and reports mentioned above cover the wider audit spectrum, similar challenges relate to cyber security as an inherently technology-focussed area of operation.
Talking to customers and auditors
Huntsman Security found similar challenges when developing its Essential 8 Auditor product through discussions with customers and the national audit bodies in the territories it operates in, as well as in conversations with leading industry analysts on the wider GRC technology landscape.
Benefits of speed
The gains from using technology to conduct data gathering, analysis and reporting are obvious – removing the need for human questionnaires, interviews, inspections and manual number crunching. Increasing the speed of the process has a number of benefits:
- You can cover larger scopes or bigger samples (even avoid sampling all together)
- You can conduct audit/assurance activities more often (weekly instead of annually)
- You can scale your approach beyond one part of the business to encompass multiple business units or even third parties
- You get answers more quickly – which for things that change continually (like patching status) means same day awareness rather than 3 weeks later
Benefits of flexibility
The ability to conduct audits across different sites or scopes, to specify different thresholds of risk for different domains, the ease of conducting audits at remote locations or on suppliers networks (especially during period of restricted travel) are ALL factors that can make technology a useful tool for the auditor.
Different parts of an organisation might have varying risk thresholds for specific controls
Benefits of transparency
One part of the FRC’s perceived problem space is that of transparency, you can ask a human how they derived a result, and they can probably tell you, or at least show you the audit trail of correspondence, meeting notes or spreadsheet calculations. But can you do this with software or technology?
Certainly, the use of AI and machine learning makes this hard, the learning nature and often black box calculations are not easy to either understand, recalculate in a repeatable way or to document. The system learns, so is always changing, and hence the rationale that a decision might not always be the same.
In technologies that are geared towards delivering audit outcomes this is easier. First, if you collect and retain data, provide an easy interface to go from results to the underlying cases in the source data, it is possible to take a score/rating/risk and reveal the specifics of what led to it. Secondly, it is vital that the calculations are transparent, i.e. that the methods of calculating risks or the way results are scored is decipherable.
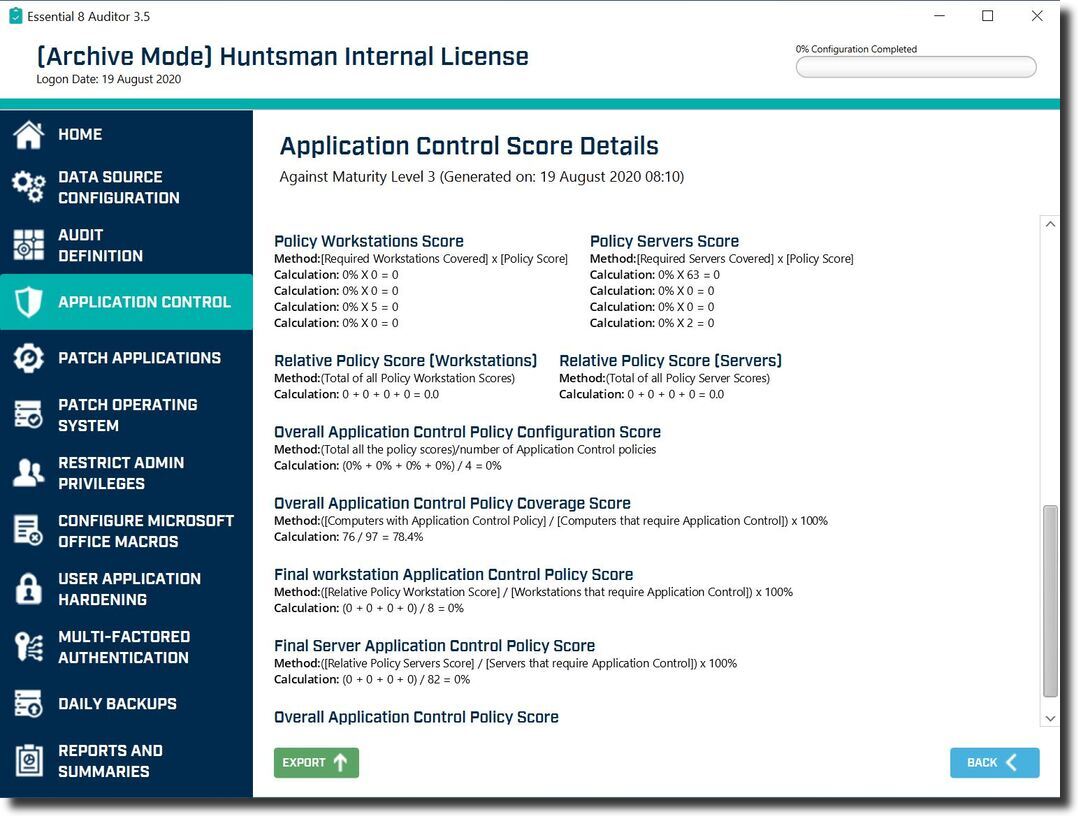
Essential 8 Auditor – Application Control Score calculation screen
Benefits of consistency
This is one obvious gain from technology, the logic is pre-programmed in. If you take two auditors and give them the same data sets or evidence case files they might draw different conclusions (possibly for valid reasons or due to them having different skill areas or experience), but the same algorithm operating on the same data will produce the same result every time.
Benefits of evidence retention
Manual evidence gathering suffers a number of drawbacks – it relies on written notes, records of verbal conversations, email trails, spreadsheets, or questionnaire responses in different formats. Retaining all this in a coherent way is difficult and going back through it even harder.
Using a consistent toolset and consistent data format means that if you need to go back to a data source from a particular network domain three months ago, you will have information that is readily available and readable. And as stated above, if the source data and evidence is re-examined using a consistent solution, you will get the same calculations, decisions and results.
Benefits of systematically generated KPIs, cyber maturity measures and issues
The outputs of any audit process need to provide details of the issues found so that the specific or general cases of the failures can be investigated and resolved. But for managers, operational teams and businesses, having a view of the KPIs for the security operations process is extremely useful.
Of course, following the “lines of defence” model, an internal or external “formal” audit might simply want the results and a level of trust in how they were calculated; however for operational management and ongoing continuous visibility, the need to derive performance statistics comes into its own.
It is worth noting that there are two dimensions to KPIs: The assessment of the strength or configuration of a control or policy (how good is the control) and the extent or level of coverage (how widely is it enforced).
To give a view of the technical maturity of a defence you really need to combine these two factors together. A weak control that is widely implemented or a strong control that provides only partial coverage are both causes for concern.
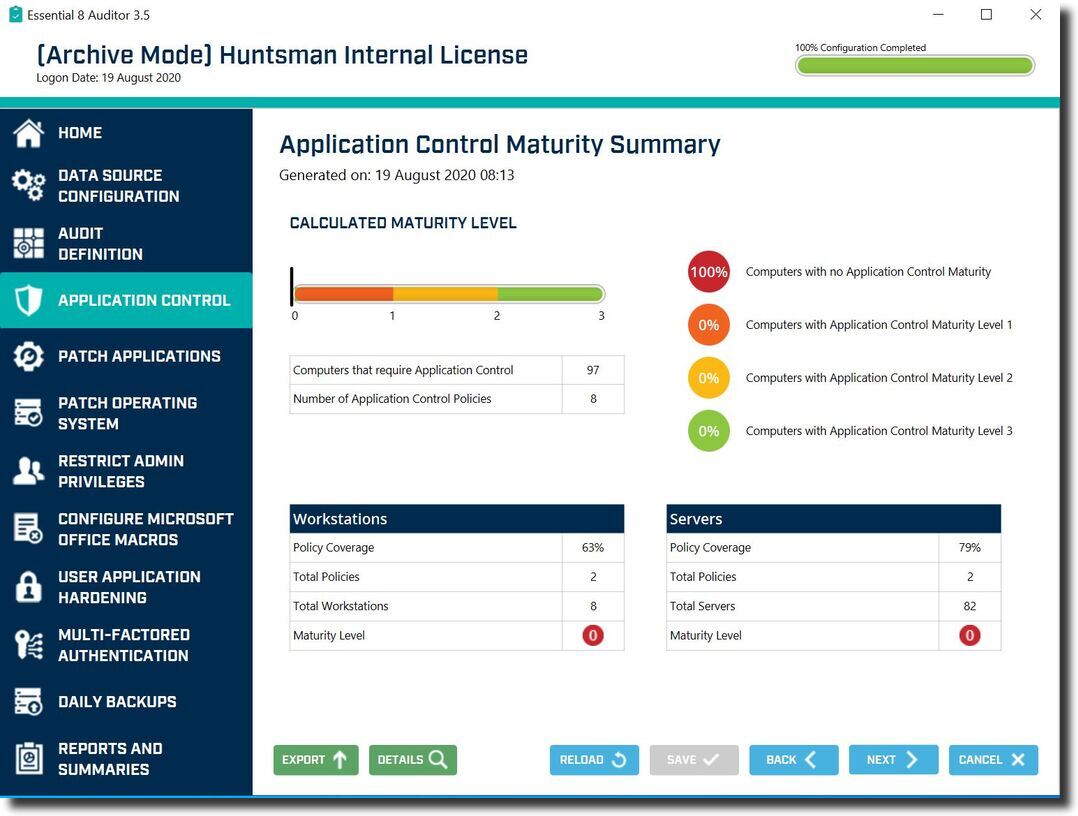
Essential 8 Auditor – Dashboard showing Application Control technical maturity calculation
Benefits of separation of process stages
The final area where technology can help is in allowing the separation and distribution of the data gathering, analysis and reporting processes. It is hard to take the data, evidence and meeting notes from someone else and analyse it. For one thing, is it trustworthy and reliable (in the case of third-party assurance questionnaires perhaps)? Then it is also hard to draw high-level conclusions about the analysis.
If technology allows the data gathering to be performed in a distributed way, say by local site administrators, third-party IT staff or non-expert users BUT in a trustworthy way, then the overhead of the audit process is much reduced. Instead of a team having to conduct multiple visits, interviews or data collection activities the toolset can be provided to the people nearest to the point of collection.
This allows the data analysis and interpretation to be performed centrally by the experts in a particular field or control area. So giving a non-expert user a way to collect and provide relevant and trustworthy audit evidence takes a large bite out of the resource overhead of conducting the audit, for both auditor and auditee.
It also means that a target organisation doesn’t have to manage the issue of allowing auditors to have access to networks, sites, data, accounts and systems to gather the audit evidence as this can be undertaken by existing administrators in the environment.
Choose the right security audit technology to boost your operation
Technology solutions in the audit process can clearly deliver benefits, however if they are too simplistic or aim to be too clever, they can simply move the problem of providing high levels of audit quality. A rapidly generated AI-based risk score is useful, but if it’s not possible to understand the calculation it is hard to either correct the control issues or trouble shoot the underlying process.
Where technology can assist the audit process, speed up data gathering and analysis, and streamline the generation of high- and low-level outputs it can be a boon.
Technology allows organisations to put trustworthy assurance into the hands of operations teams and managers, consultants and auditors alike to provide flexible, rapid and frequent views of control data and understanding of risk posture. If this can be done in a way that is cognisant of the risks and challenges as we have shown, then auditors and regulators such as the FRC can be satisfied.
 About Huntsman
About Huntsman





