Believe it or not, a year has passed since the EU’s General Data Protection Regulation (GDPR) became law. Over that year, the impact of the legislation has spurred countries around the world to review their own privacy laws to enforce an equitable tightening up of their own data protection approach; but how effective has this year been in terms of making our personal data less at risk of being stolen and sold on the black market?
Security and Privacy complement each other, but remain different
Many believe security and privacy have a similar strategic mandate, yet GDPR has demonstrated that the difference between the two is greater than most realise. The issue of keeping customer information private and the degree to which you are responsible for the collection and use of that data has become a hot topic in most businesses, since the focus of regulators, coupled with hefty fines, has seen executives and directors take note.
Privacy management, in some cases, has become the focal point of security programmes, since security certainly supports an organisation’s privacy ambitions. Security, however, is just a subset of a wider business problem, which GDPR represents well in its regulation. GDPR is undoubtedly the most stringent privacy legislation on the planet, and it’s made other jurisdictions outside of the EU act quickly (and some might say hastily) to align with its intent.
The key 5 cyber security clauses within GDPR
GDPR has just five cyber security clauses [1] buried in the total of 99 requirements organisations need to comply with:
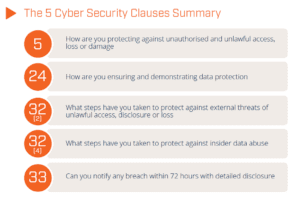
GDPR 5 Cyber Security Clauses
With these five security requirements at the heart of GDPR, one might assume most organisations with an existing security programme could easily achieve compliance. Yet even one year on and consumer awareness at an all-time high, there still seems to be problems for companies trying to become compliant. The problem is that security is just one viewpoint of any business’s overall approach to privacy, yet some organisations focus on security rather than the requirements as laid out by GDPR and their local data protection authority.
The European Commission GDPR statistics
The European Commission responsible for GDPR published some interesting statistics[2] relating to the first year of this new legislative framework. For starters, just over half of EU citizens they surveyed know there is a country-specific data protection authority responsible for protecting their privacy rights. Furthermore, even with the half aware that there is a public authority, just twenty percent of them know which public authority they should speak to.
In this first year, the European Commission received 144,376 queries[3] and complaints from the various data protection authorities scattered throughout Europe. The data breach notification numbers are frightening, with 89,271 lodged notifications since 28th May 2018. In this case, the definition of a data breach is when, “personal data for which a company is responsible is accidentally or unlawfully disclosed,” and that company must, “report this data breach to their national data protection authority within 72 hours of finding out about the breach.”
In terms of penalties, GDPR affords data protection authorities the power to dish out fines of up to 4 % of the company’s turnover. The European Commission provided some anonymous (but guessable) examples of the fines they have doled out since May last year:
- A social network operator was fined € 20,000 for failing to secure users’ data;
- Google was fined € 50,000,000 for lack of consent on advertisements;
- A data brokering company was fined € 220,000 for failing to inform citizens that their data was being processed by the company;
- A sports betting cafe was fined € 5,280 for unlawful video surveillance;
- A Lands Authority was fined € 5,000 for failing to ensure the necessary security for their data processing.
One of the biggest issues that authorities have had to deal with, is that many of the companies they are investigating or prosecuting, such as social media platforms, offer services in more than one EU country simultaneously – and in some cases it could be all EU member states. The European Commission has mandated that in many cases, one national data protection authority takes the lead in the investigation, whilst the other provides supporting resources. Any disagreement falls back to the Commission to arbitrate.
Data breaches are still caused by security problems
Most notifiable breaches over the past year are still fundamental security failures, be they as a result of successful phishing campaigns, exploits used against known unpatched vulnerabilities or simply employee carelessness. We’ve seen the same set of root causes in Australia, and since more breaches than ever are being reported there are robust statistics that show Australia aligns, in terms of its susceptibility to these issues, with the rest of the world.
The five key security requirements listed earlier in this article still cause headaches for many organisations. These requirements state several specific outcomes, but there is an overarching key theme spanning them all: watch what’s going on within your enterprise and alert your security team when something doesn’t look right.
Even that first requirement, “How are you protecting against unauthorised and unlawful access, loss or damage?” is addressed by implementing robust identity and access management systems, coupled with comprehensive auditing and alerting.
Gear up to meet the 5 cyber security clauses of GDPR
Is your organisation able to fulfil the 5 cyber security clauses of GDPR? Do you have technology that can help you meet your obligations? By having a Security Information and Event Management System (SIEM) that can monitor your entire enterprise for unusual or malicious activity, you can alert your security team when suspicious patterns of activity threaten the security of your data.
You always need to know where your data is, what level of security it requires (how sensitive is it) and who should have access to it. Only by fully understanding the lifecycle of your data can you hope to be GDPR compliant or meet the requirements of your own country’s local data protection legislation.
[1] If you want more information on how to address these five cyber security clauses, you can refer to our whitepaper, “Fast Track your GDPR Compliance: How to Implement the 5 Essential Cyber Security Requirements of GDPR.”
[2] https://ec.europa.eu/commission/sites/beta-political/files/infographic-gdpr_in_numbers_1.pdf
[3] It’s important to note this is indicative and not entirely accurate. Actual numbers are not verified since they can only report on the ones they have been informed about. It’s likely a higher number with cases being handled locally.
 About Huntsman
About Huntsman