On-demand cyber vulnerability and maturity assessment
Huntsman Security’s Essential 8 Auditor provides directors and senior executives on-demand reporting of their organisation’s security posture in minutes.
Request a live demo with a Huntsman Security Expert today, and you will get:
- Use cases to help improve your security posture
- Answers from our experts around your cyber security strategy
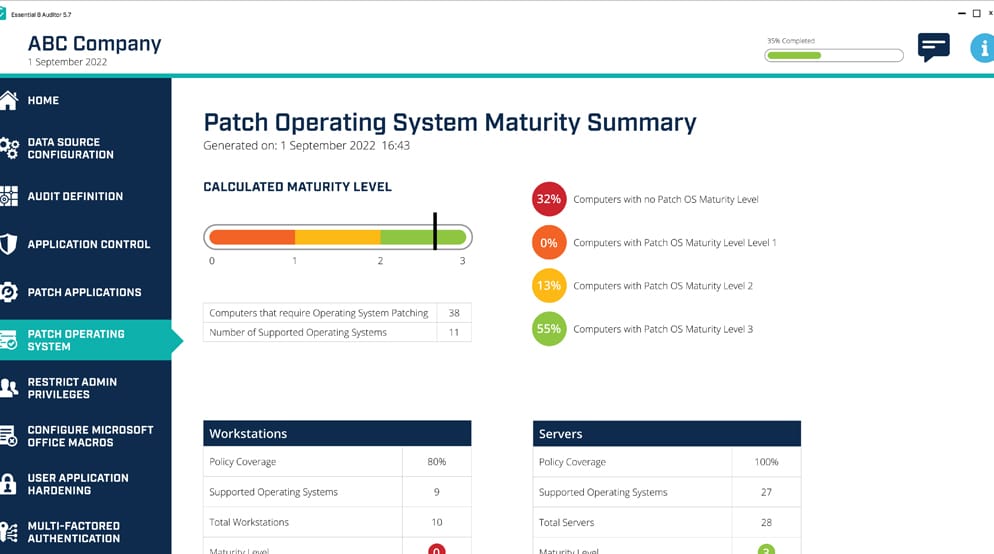
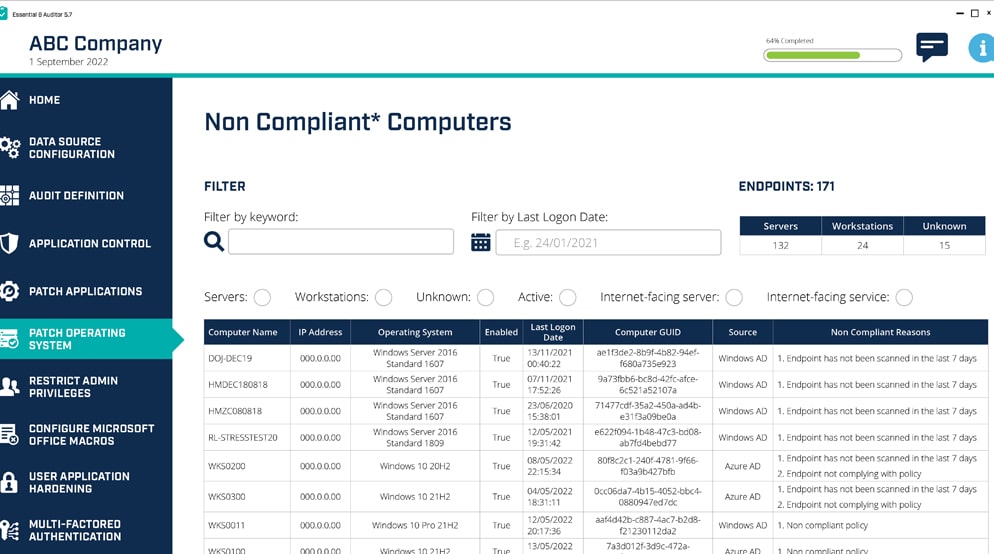
- Insights on aligning with the ACSC’s Essential Eight security controls